

SOCaaS
Get cyber resilience
24 х 7 х 365
with SOC as a Service from Octava Defensee
Benefit from continuous monitoring, investigation
and prompt response to cyber threats.
How SOCaaS works?
Сonnecting to Octava Defence’s SOC involves outsourcing the routine task of infrastructure monitoring and getting access to professional cyber analysts to implement investigation and response processes.
SOCaaS
We are here to help you fill the cycle of complex cybersecurity approach
MONITORING
Analyze protection objects 24/7 and notify the IT service of deviations according to SLA requirements
INVESTIGATION
RESPONSE
Contain and counteract the development of the attack and break the kill chain at the start
TECHNICAL, OPERATIONAL, AND ORGANIZATIONAL SUPPORT
Operate by risk approach and prevent risks by enhancing the efficiency of technologies usage in operational, human and organizational perspective
МОНІТОРИНГ
Спостерігаємо за подіями 24/7 та повідомляємо ІТ-службу про відхилення відповідно до вимог SLA
РОЗСЛІДУВАННЯ
Аналізуємо хронологію подій, визначаємо можливі вразливості або інциденти та визначаємо що і чому відбулося
РЕАГУВАННЯ
ТЕХНІЧНА, ОПЕРАЦІЙНА ТА ОРГАНІЗАЦІЙНА ПІДТРИМКА
Запобігаємо ризикам, підвищуючи ефективність використання технологій, операційну та організаційну зрілість служби кібербезпеки.
Octava Defence
Reviews

«Thanks to Octava Defence, we detect and stop attacks long before they spread»
Vyacheslav Nehoroshikh
CIO of FOXTROT GROUP

«Cooperation with Octava Defence provides a reliable result - a significant long-term increase in cyber resilience, regardless of the types of threats»
Sergey Lukyanenko
СІSO of LIGA Group

«Using SOC as a service from Octava Defence is captivating in that it allows you to quickly get an independent team of experts and ready-made cybersecurity processes. At the same time, use them in sufficient amount for the organization»
Aleksandr Atamanenko
CISO of Octava Group
SOCaaS
Why do you need a SOC?
- technologies used;
- staff training;
- necessary processes.
- increasing the technological transparency of the corporate infrastructure;
- increasing the speed and quality of incident recognition;
- improving the efficiency and speed of response to incidents;
- eliminating the causes of incidents;
- implementing tbe process model for managing cybersecurity.
SOCaaS
SOC tools & technology model
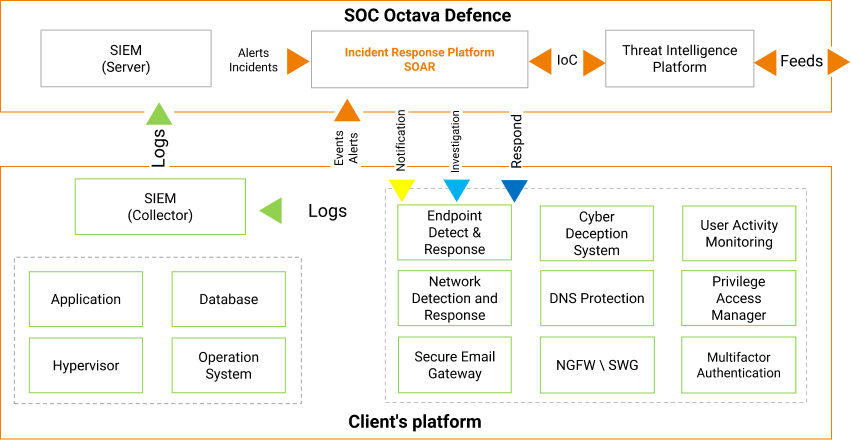
IDENTIFICATION
- OSINT
- Pentest (Black/Gray Box)
- Assets Management
- Vulnerability Management
- Patch Management
SOC-READY PROTECTION
- Security Compliance Audit
- Breach Attack Simulation
- Data Leak Prevention
- End-Point Detection and Response
- Network Detection and Response
- Cyber Deception Systems
- Privileged Access Management
- User Behavior Analysis
BASIC PROTECTION
- Endpoint Protection (Antivirus)
- Multi Factor Authentication
- Next Generation Firewall
- Secure Email
- Web Gateway
- DNS Protection
- Web Application Firewall
- Sandboxing
MONITORING
- SIEM
- Threat Intelligence Platform
- Security Orchestration, Automation and Response
Do you have any questions?
Write to us
Contact us
Contacts

Sales department
+38 044 538 00 45

General questions
+38 044 538 00 40

infosec@octava.ua

Central office
