The term Defensible Network Architecture (DNA), was first introduced by cybersecurity expert Richard Bejtlich in 2004 in his book The Tao of Network Security Monitoring.
Richard Bejtlich is a graduate of the US Air Force Academy and has held the positions of Chief Security Officer at FireEye, Chief Security Officer at Mandiant, and worked at General Electric, where he created and led the 40-person GE Computer Incident Response Team (GE-CIRT). He is currently a strategist and author at Corelight.
R. Bejtlich defines a Defensible Network as an information architecture that is monitored, controlled, mitigated, and kept up to date.
Octava Defence believes that this approach allows you to look at the issue of cyber security implementation systematically and with an understanding of how certain principles can be implemented in your organisation.
The main points of implementation of the DNA concept are described in more detail below in the order of increasing complexity from 1 — the simplest to 7 — the most complex model.
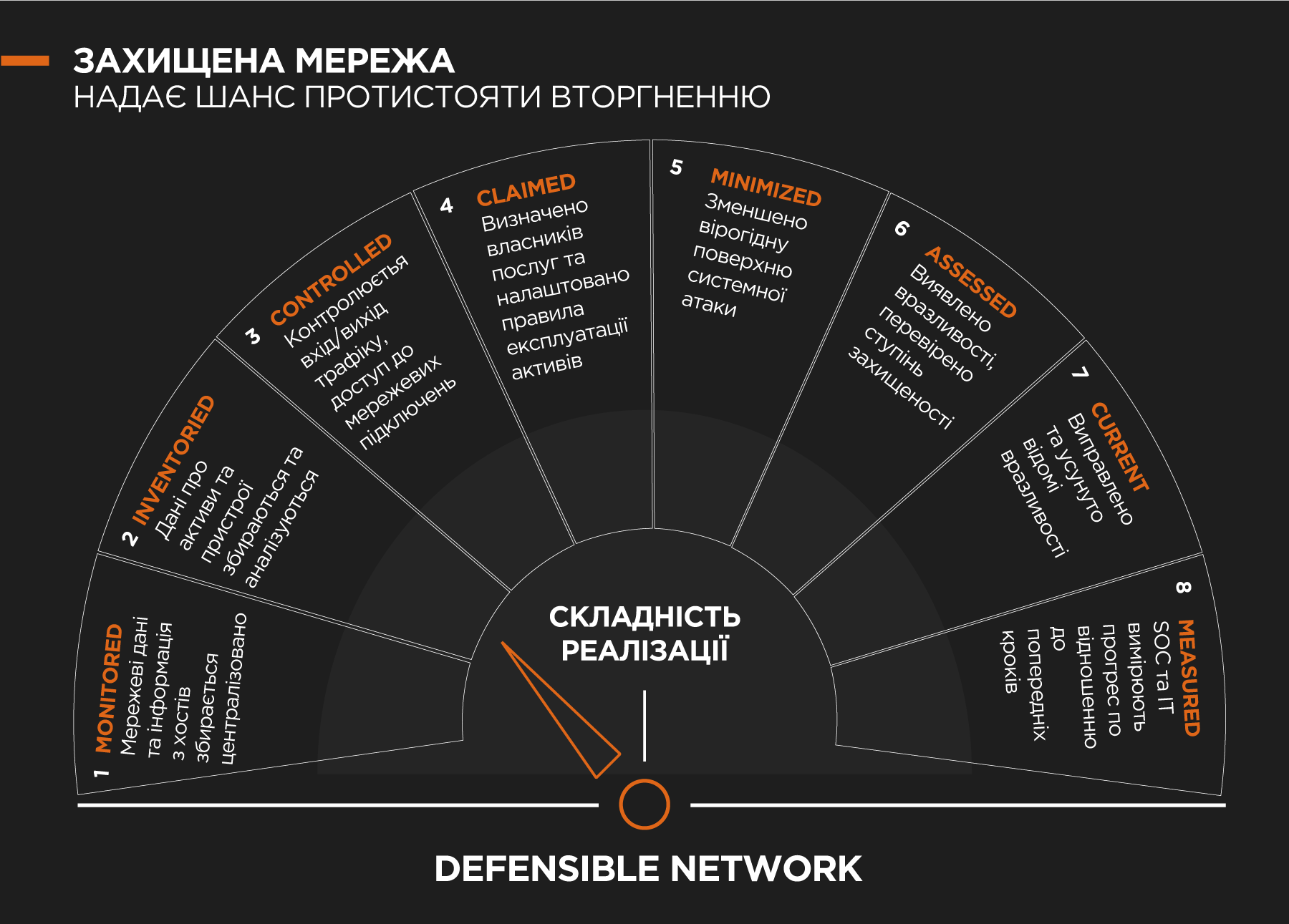
1. Monitoring. The easiest and cheapest way to start implementing DNA in an enterprise is to implement the monitoring function. To do this, you need to deploy a system of network security monitoring sensors that collect as much information as possible from various points in the network, including the firewall/router/IPS/DNS/proxy, etc. More complex types of data (requiring reconfiguration of assets and the purchase of large databases) should be saved for the future.
2. Inventory. You need to be very aware of what you post on your network. If you have already implemented monitoring, you will be able to obtain most of this information in a passive mode. This item is new in DNA 2.0.
3. Control. Once you have a thorough understanding of your network, you can start implementing network controls. This can be done in any way — incoming or outgoing filtering, network access control, proxy connections, etc. The idea is that you’re moving from a network architecture where everything flows through to a new concept where any activity is authorised as far in advance as possible.
4. Approval of rights. This includes the identification of asset owners and the development of policies, procedures, and plans for the operation of the asset itself. The point is that it is easier to implement strict controls than to make people take responsibility for the integrity of the system.
5. Minimising losses. This step directly affects the configuration and condition of the assets. The goal is to reduce the attack surface of network devices. This approach can be applied to clients, servers, applications, network equipment, and more.
6. Evaluation. At this stage, weaknesses in assets are identified. To begin with, you need to disable unnecessary services after conducting a detailed analysis. It is also necessary to simulate the actions of an attacker to verify the overall security operations.
7. Installing patches and updates. This item means that your assets should be set up and configured so that you can withstand known attacks by patching the vulnerabilities found. It is better to disable a set of functions that no one uses.
Since updates can sometimes disrupt the operation of applications, this step should be performed last.
The method described above increases the chances of successfully resisting an intrusion and is suitable as a multi-year strategic programme for any organisation seeking to improve its cyber security.
Need help in implementing the DNA concept?
Richard Bejtlich’s book «The Practice of Network Security Monitoring Understanding Incident Detection and Response, will be useful for you».
Or contact Octava Defence consultants for advice:
+38 044 538 00 45;
infosec@octava.ua